On the iPhone 4 pre-order day Apple and AT&T pre-order websites crashed! This was kind of traffic the websites had. Within first week of iPhone pre-order, Apple sold 600,000 iPhone 4 units. Since 2007, Apple has rolled out 4 different versions of the phone. All of them are very popular and consumers love them. To begin with, the non-executive users were mostly using iPhone. But with iPhone 3G the things seem to have started changing.
Consumers love it, and executives love it too! IT teams struggled to accept the iPhone in the enterprise due to various policy non-compliances. The iPhone was still considered as an unsecured/ non-enterprise device. This situation seems to be changing with Apple’s announcement of iOS4. The BackBerry is considered the most enterprise savvy device to date. But iOS4 based iPhone and the future iOS4 iPad are presenting a serious challenge to the BlackBerry dominance.
This document briefly discusses a few key points about why the situation is changing and why iPhone is becoming more widely accepted device in the enterprise. This write-up purely focuses on the enterprise support provided by iOS4 mobile operating system and the iPhone/ future iPad devices running it. The information in this article is based on the various developer preview tools and information published by Apple for iPhone developers.What is an enterprise device?
To be accepted in an enterprise, a mobile OS/ device should satisfy following minimal requirements -
- Mobile Device Management
- Security and Control over data
- Over the Air Application distribution and management
The MDM (Mobile Device Management) capability is a mandatory requirement for any device to be labeled as an enterprise device. The ability to control the device in terms of resource access, configurability, and application management are the key features of any MDM solution. There are already dozens of known solutions that exist in the market. However, without the support from iPhone OS, none of these solutions could really “manage” the iPhone OS based devices.
The other most important feature than an enterprise device should have is – support for stringent data security and custom connections to support VPN/ SSL and industry wide accepted security protocols. No enterprise wants the data being transported to be seen/ tampered when it is consumed over the air.
The ability to install/ uninstall/ upgrade the private enterprise applications remotely on the device makes the third most important requirement for an enterprise device.
The other features of an enterprise device would consist of – ability to sync with corporate mail servers, ability to configure multiple mailboxes, delegated calendars etc. There are many other requirements that can be listed but these are the most common and must-haves.
So let’s evaluate iPhone (iOS4) based on these criteria.
MDM Support in iOS4
The recent launch of iOS4 makes it much easy for IT staff and enterprise developers to manage iOS4-based devices. All the iPhone 4 devices and future iPad devices shall have the iOS4. With the free upgrade to iOS4, all the older iPhone 3G and 3GS phones shall also be manageable under enterprise MDM. The enterprises now have the option to use the third party MDM servers like Sybase Afaria, CloudSyncSaaS, MobileIron, BoxTone, Zenprise that will leverage the iOS4 capabilities. Alternatively the iOS4 features help the enterprises to build a small custom solution that will help manage the iOS4 devices effectively. In iOS4, apple has offered the simplified device management, OTA device enrollment, enhanced control over the device in a transparent manner and simplified OTA delivery of the enterprise applications.
The custom MDM solution/methodology offered by iOS4 looks to be an ideal solution that uses the SCEP service. This enables the solution to leverage the SCEP services offered by any OS. Microsoft Windows Server based SCEP service is an example, however the model ensures that it is not mandatory to go with Windows server. The MDM services, over the air (OTA) app distribution features offered by iOS4, combined together acts as a value add to the overall solution.
So let’s first see how exactly the MDM services are available in iOS4 and how to utilize them into our custom solution.
Apple allows manage the device in three easy steps –
- Configure
- Enroll
- Manage
How it works?
The following diagram explains the technical steps/phases of the device management (source – Apple developer documentation) -

The XML based plist like configuration profile allows IT staff to specify the constraints/ permissions that a device will have. This configuration can be prepared using XML with proper syntax. The process can also be automated with the help of a custom webpage that builds this XML based on the needs. Enterprises can prepare the generic configurations or user specific configurations, as the case may be, based on their needs. The configuration profile then needs to be delivered to the device using Simple Certification Enrollment Protocol (SCEP) via web server/ web page. The web server should be configured to integrate with the Active Directory Services in order to authenticate the users and choose the right configuration profile. The profile will then be delivered over the air in an encrypted format.
Below is the workflow to explain these steps –- IT Staff configures the SCEP server. A SSL secure and ADS authentication integrated webpage to access the profile to user is deployed.
- Send a SMS to the target device with the URL to access the enrollment server configured.
- On the iOS4 device, user taps on the URL in the received SMS – it opens the safari browser on the device.
- Since the URL is configured to authenticate user with Active Directory Services, it shall ask user to enter the user name and password.
- Once the user is authenticated, the screen shall turn into the configuration profile installation. This dialog explains what exactly is happening and gives an idea of what is going to happen once the installation is accepted. Mind you – this is the chance for the user to decline if he/ she do not want the device to be enrolled!
- The installation here onwards is automatic – all the steps explained in the above diagram takes place without any manual intervention.
- At the end, the configuration profile gets installed on the device, and the device is successfully enrolled in the network!

The configuration profile helps IT staff to specify various policies that include –PasscodePolicies, Access Restrictions (such as Youtube, Safari launch, iTunes Music Store access, Camera access permissions, Application installation permissions and so on), WiFi configuration, VPN configuration, Email account configuration – Exchange and non Exchange, LDAP access, Calendar configuration (self and subscribed/ delegated), Web Clips (these are like safari bookmarks on your home screen), PKCS Certificates and Credentials, SCEP payloads and APNs. Profiles can be signed and encrypted for secured delivery. The encrypted profiles can be installed only using the SCEP services.
The configuration profiles can be built using the utility called iPhone Configuration Utility – iPCU. Read more about this tool at – http://support.apple.com/kb/DL851
Now once the initial configuration is over, IT staff can continue to monitor the device, update the configuration profiles as the policies may change. This is easily achieved by using Apple’s push notification services. The events can be configured on the enterprise server to include the PUSH notifications that will wake up the device and have updated profiles installed.
The MDM Services in association with proper configuration profile provides two powerful functions - Remote Commands and
- Queries
- Ability to control device,
- Ability to lock down features/ services
- Enforce stringent security policies/ rules of network, VPN configuration
All the commands can be delivered to the phone via MDM services configured using custom profiles and push notifications!
The Query is designed to provide the necessary device information. It enables IT staff to gather a good amount of device information , which include –
- Network details - Bluetooth and Wi-Fi MAC addresses, ICCID, Current and SIM carrier network, Carrier settings version, Phone number, Data Roaming setting (on/off )
- Device information - Device name, UDID, IMEI, and serial number, Model name and number, OS and build version, Modem firmware version, Total capacity and free space
- Application details - List of apps installed, App ID, name, and version, Size of app and its data, Provisioning Profiles installed and their expiry dates
- Compliance and security information - Installed Configuration Profiles, Certificates and expiry dates, List of restrictions in effect, Data Protection capability, Password compliance
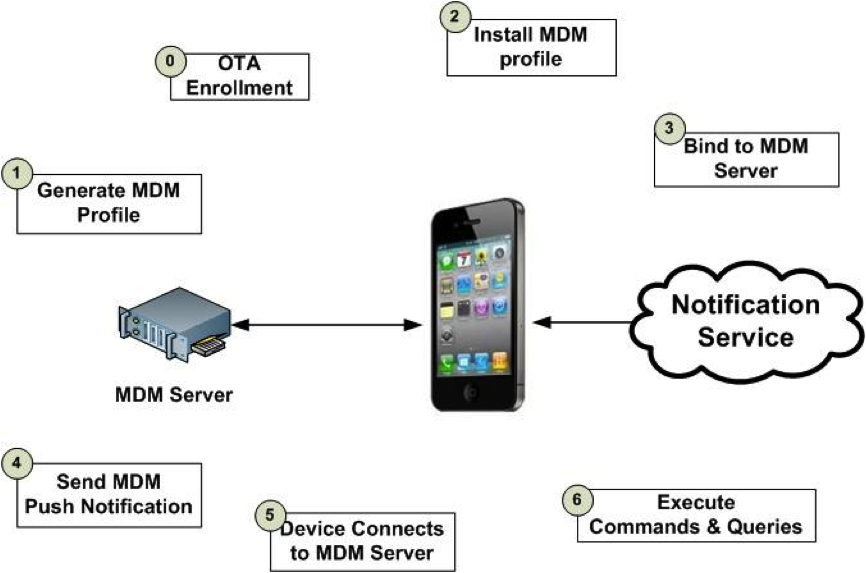
Every time there is a change in the policy or configuration and PUSH notification can be initiated that will carry the profile and its payloads.
iPhone Configuration Utility -
This tool is an easy to use and configure any iOS4 based device. You can find the detailed review article at -http://www.macworld.com/reviews/product/412719/review/iphone_configuration_utility.html
Wireless App Distribution
MDM helps manage the device and its association/ compliance in the enterprise network. What’s the fun in using the device if you are not able provision your enterprise application on them? And this is where Apple has offered the Wireless Application Distribution mechanism for the enterprise application without going onto the App Store. Yes, you need not submit your application to the app store in order to have them installed on the enterprise iOS4 devices. All a developer needs to do is, build the application, and publish the .IPA with a XML manifest file to tell about application and Ad-hoc distribution provision file on the server so that is talks to MDM server. This is same ad-hoc distribution profile developer used to give away for marketing and QA teams to install the apps using their iTunes. This time, it’s going to be over the air.
Note that in order to have wireless app distribution work on your device; the device NEED NOT be managed under MDM as we saw above! In Endeavour we use this mechanism to offer the test applications and releases to our enterprise customers during testing phase. Once the app is hosted on the server, an email or SMS with the webpage link is sent to the target device. The webpage is secured with our Active Directory logins that are shared with them. They open the URL and it turns out to be their mini App Catalog!
At a later date we plan to setup a simplified and custom built App catalog for our enterprise customer to host all the applications of the enterprise in their own network. The user authentication and ADS integration will be part of this catalog.
Now if you already have MDM it helps – the life is easy! See the scenario below –- Device is being managed under MDM Server
- IT Staff configures a web clip to be delivered to the device on the MDM server. This web clip has list of Enterprise apps that are private in the network!
- The web clip appears on the device as App catalog (because you named it so!). User opens the App catalog and sees the list of applications being delivered in your network!
- Taps onto one of the apps, and the application starts downloading! And there you are – you have the application to your phone over the air.
- MDM still helps you to update that provision profile whenever it is renewed.
How iOS4 works with existing infrastructure?
The important fact is that with iOS4, nothing changes in the existing network infrastructure. If you would have observed – Apple MDM support is purely based on SCEP services – this is the basic service you would find in any network resource like routers. So for Network Administrators it should be as simple as monitoring your CISCO router! The difference is in the comfort level of the UI. If Enterprises can build the MDM services themselves on top of existing MDM commands and queries offered in iOS4, they would have what they exactly needed.. The alternative is to go with third party MDM server platforms that are sold as products.
For various reasons that involve time and cost, the best approach might be to invest in the existing off the shelf components and fine-tune them to your needs. The MDM and wireless app distribution will have to be built inside the business workflow seamlessly!
No change is expected to happen in any of the enterprise access scenarios including changes to exchange Active sync, VPN and other policies, as Enterprises embrace iOS4. In a short period of time, we can expect the existing MDM solution vendors to tailor their products in such a manner that these products leverage the benefits of the iOS4 to support the iPhone and future iPad devices.
More Enterprise Support in iOS4/ iPhone -
As an add on to the iOS4 upgrade, the device gets some of the below cool features –VPN Support - Network communications stay secure with Cisco IPSec VPN, WPA2 Enterprise Wi-Fi, Support for SSL/TLS on iPhone, Multiple mailboxes with unified view, Enhanced Calendar support.
Links and References:
- iPhone OS Enterprise Deployment guide (http://manuals.info.apple.com/en_US/Enterprise_Deployment_Guide.pdf)
- WWDC 2010 Sessions
- iPhone and OTA enrollment configuration guide (http://images.apple.com/iphone/business/docs/iPhone_OTA_Enrollment_Configuration.pdf)
- Apple Discussion Forum (http://discussions.apple.com/thread.jspa?threadID=2198458&start=0&tstart=0)
- Microsoft SCEP Implementation Whitepaper (http://www.microsoft.com/downloads/details.aspx?FamilyID=E11780DE-819F-40D7-8B8E-10845BC8D446&displaylang=en&displaylang=en)
- Active Directory CS Step-By-Step guide (http://www.microsoft.com/downloads/details.aspx?familyid=44315BFF-B744-4637-A66B-E69B4955EE45&displaylang=en)